
Our services
From consulting and strategy development to implementation and support, our comprehensive services can help your business thrive.

Cybersecurity
Proactive Risk Management & Threat Intelligence
In today's interconnected world, cybersecurity is not just about reacting to breaches but proactively preventing them. ACP-Consulting implements comprehensive risk management frameworks, including threat modeling and vulnerability assessments, to identify and mitigate potential attack vectors before they can be exploited. We leverage advanced threat intelligence to stay ahead of emerging cyber threats, providing your organization with the foresight and defenses needed to protect critical assets and maintain business continuity against a constantly evolving landscape of adversaries.
Cybersecurity Risk Management Framework
Effective cybersecurity starts with a structured risk management framework that links threats, vulnerabilities and business impact. This framework defines assets, evaluates risks, sets security objectives and guides which controls and processes should be implemented first. It turns cybersecurity from a purely technical activity into a business‑driven discipline that supports continuity, compliance and resilience.
ACP‑Consulting helps organizations build a practical, risk‑based cybersecurity program tailored to their size, sector and regulatory environment. We work with you to identify critical assets and data, assess current controls, perform gap analyses and define a prioritized roadmap of improvements. The result is a clear, governed cybersecurity framework that supports informed decisions and aligns protection efforts with your real business priorities.





Defense‑in‑Depth and Security Operations
Modern cyber defense relies on a layered approach: preventing attacks where possible, detecting suspicious activity quickly, and responding in a structured way when incidents occur. This “defense‑in‑depth” methodology spans policies, identity and access management, endpoint and network protection, monitoring, incident response and recovery procedures. It ensures that if one layer fails, others still protect your systems and data.
ACP‑Consulting designs and optimizes these layers so that people, processes and technology work together as a cohesive security operations capability. We help define security policies and standards, strengthen access controls, select and tune security tools, and establish monitoring, alerting and playbooks for incident handling. This integrated approach improves visibility on threats, reduces response time, and supports continuous improvement of your security posture.
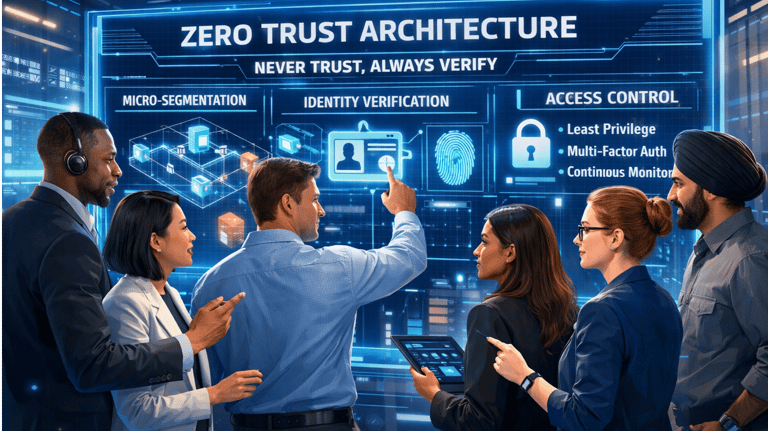
Zero Trust Architecture (ZTA): The "Never Trust, Always Verify" Model
In today's complex, perimeter-less environments, traditional security models are insufficient. We specialize in designing and implementing Zero Trust Architecture (ZTA), a modern security framework based on the principle of "never trust, always verify"
General View of the Framework
ZTA eliminates the concept of implicit trust that is typically granted to users and devices inside a network perimeter. Instead, every access request—regardless of where it originates—is treated as hostile and must be verified before access is granted. This approach significantly reduces the attack surface and limits the lateral movement of threats within your network. Our methodology focuses on micro-segmentation, least-privilege access, and continuous verification.
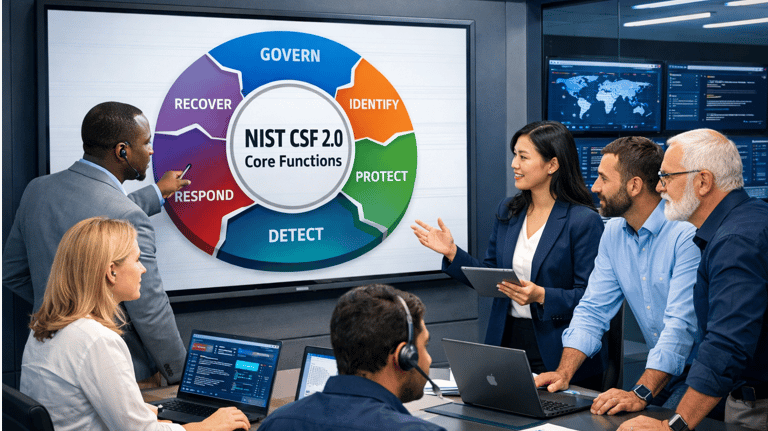
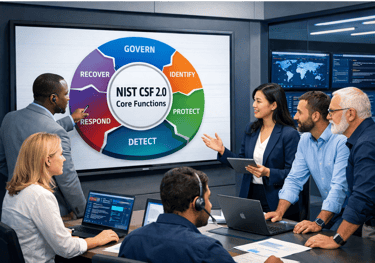
The NIST Cybersecurity Framework (CSF) 2.0: A Holistic Risk Management Approach
We utilize the NIST Cybersecurity Framework (CSF) 2.0 as our primary methodology for assessing, managing, and improving your cybersecurity risk. This framework provides a flexible, risk-based approach that is adaptable to organizations of all sizes and sectors .
General View of the Methodology
The NIST CSF 2.0 is structured around six core functions that provide a high-level, strategic view of an organization's management of cybersecurity risk. Our service helps you implement and mature capabilities across all six functions, ensuring a comprehensive and continuous cycle of security improvement. This holistic approach ensures that security is integrated into your overall business strategy, not treated as an isolated IT function.


ISO/IEC 27001 and the Information Security Management System (ISMS)
For organizations requiring formal certification and a structured, auditable approach to information security, we implement the ISO/IEC 27001 standard. This framework establishes, implements, maintains, and continually improves an Information Security Management System (ISMS) .
General View of the Methodology
The ISMS is a systematic approach to managing sensitive company information so that it remains secure. It includes people, processes, and IT systems by applying a risk management process. Our methodology is based on the Plan-Do-Check-Act (PDCA) cycle, ensuring that your security controls are continuously reviewed and optimized to address evolving threats and business requirements. Achieving ISO 27001 compliance demonstrates a world-class commitment to information security to your clients and partners.

